
Why Your Organisation Should Adopt the Essential 8

Duong Dang
30 June 2025
Table of Contents
- Threats to Australian organisations are real
- Penalties for Australian organisations can be $50m+
- Provides a minimum baseline and pathway to ISM, ISO27001 and NIST
- Implementation guidelines are prescriptive
- The Essential 8 can be self-assessed or externally assessed
- Constantly updated by the Australian Cyber Security Centre (ACSC)
- Win customers
- Resources
The Essential 8 is a minimum baseline for Australian organisations to protect and recover from cyber incidents. It is a starting point for cybersecurity and is constantly updated by the Australian Cyber Security Centre. This publication explores 7 reasons why your organisation should implement it. The Essential 8 is not a complete framework but it is a good starting point.
Threats to Australian organisations are real
The threats to Australian organisations from cyber attacks are real and have been highlighted by recent high-profile attacks on companies such as Optus and Medibank. These attacks resulted in the loss of millions of personal identifiable information, with Optus losing 1.2 million customers' current forms of identification through an API breach. The head company of Optus, Singtel, set aside $140m for customer remediation activities in response to the attack.
Medibank, on the other hand, lost all 9.7 million of its data personal identifiable information, including health claims data from its customers. This resulted in a 20% drop in Medibank's share price, which equates to around $2bn in market capitalisation, not to mention the reputational damage the company suffered.
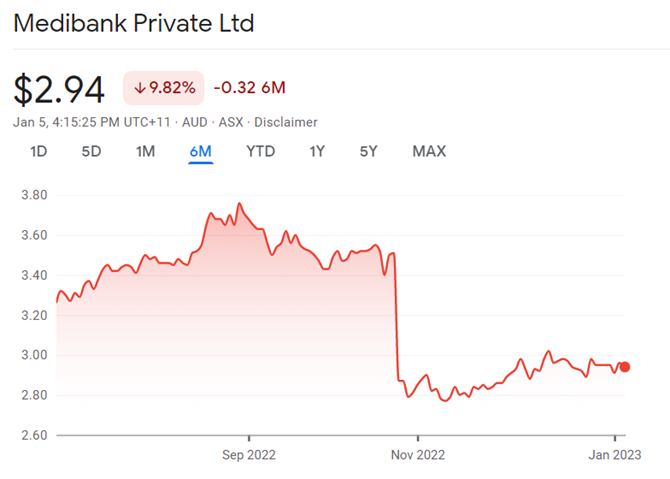
Source: Google Finance
The Australian Cyber Security Centre (ACSC) has also released recent figures showing an increase in cyber attacks and the value of cyber attacks. In the past year, the cost of business email compromise alone was $98m. Additionally, there was a 14% rise in the average cost per cybercrime reported, with small businesses losing an average of $39k, medium businesses losing $88k, and large businesses losing $62k. There was also a 25% increase in new Common Vulnerabilities and Exposures (CVEs) and a 13% increase in the number of cybercrime reports. On average, a cybercrime is reported every 7 minutes. The states of Queensland and Victoria were found to have the highest number of cybercrime reports.
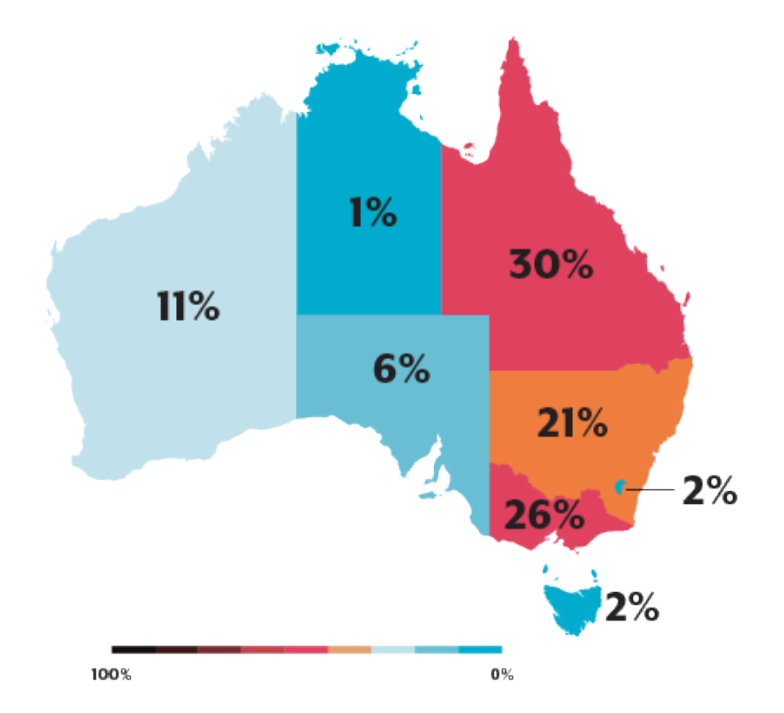
Source: Australian Cyber Security Centre (ACSC)
Furthermore, medium-sized organisations are losing more than large businesses as they are less likely to apply cyber mitigation strategies. Medium-sized organisations might also be less likely to report cybercrimes, which can contribute to the problem.
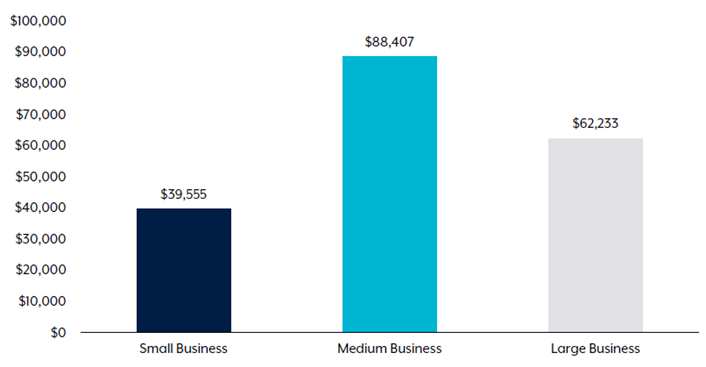
Source: Australian Cyber Security Centre (ACSC)
Penalties for Australian organisations can be $50m+
The Australian government has recently taken steps to address the growing threat of cybercrime by announcing increased penalties for companies involved in high-profile cyber threats. This move comes in the wake of recent attacks on major Australian companies such as Optus and Medibank. The Privacy Legislation Amendment (Enforcement and Other Measures) Bill 2022 increases penalties for such incidents to whichever is greater of: $50 million, 3x the value of any benefit obtained through the misuse of information, or 30% of a company's adjusted turnover in the relevant period.
The government's decision to increase penalties for cybercrime is a significant step towards deterring future attacks and holding companies accountable for their actions. The recent attacks on Optus and Medibank have highlighted the need for stronger measures to protect both individuals and businesses from cybercrime. The attacks resulted in the loss of personal information and had a negative impact on the companies' reputation and financial stability.
In response to these attacks, the government has established a taskforce to combat cybercrime and has commissioned a report on the Optus and Medibank incidents by the Cyber Security Co-operative Research Centre. The taskforce will be responsible for identifying and investigating cybercrime, and will work closely with law enforcement agencies and the private sector to develop strategies to combat cyber threats.
Furthermore, additional legislation is expected to be implemented as the government aims to make Australia a leader in cybersecurity. This includes measures to protect personal information and strengthen cybersecurity regulations for businesses. The government is also investing in research and development to improve cybersecurity technologies, such as artificial intelligence and machine learning.
Provides a minimum baseline and pathway to ISM, ISO27001 and NIST
The Essential 8 is a set of minimum baseline cyber security measures to protect organisations from cyber threats. It is not a standard or a framework, but rather a collection of essential mitigation strategies that have been determined to be the minimum baseline for protecting against cyber incidents. The Essential 8 was developed based on the threats that the ACSC saw and determined to be the most critical to address.
The Essential 8 includes strategies to mitigate cyber security incidents and aligns with the Information Security Manual (ISM), which can be found on the ACSC website. The Essential 8 can also be used as a stepping stone towards other popular cyber security frameworks such as ISO 27001 and the National Institute of Standards and Technology (NIST) framework. These frameworks are more holistic in nature, recognising that solutions to cyber security are not simply technology solutions, but require a comprehensive approach to address people, process, and technology.
Organisations should aim to implement more robust cyber security measures beyond the Essential 8 to provide a more comprehensive defence against cyber threats. Additionally, implementing the Essential 8 does not guarantee complete protection against cyber threats, but rather provides a strong foundation to build upon as cyber threats continue to evolve.
Implementation guidelines are prescriptive
The implementation guidelines for Essential 8 are prescriptive in nature, making it easier for organisations to implement the measures. The implementation guidance developed by the ACSC is specifically designed for Microsoft based organisations, which are typically medium to large-sized organisations. This guidance can be found on the ACSC's website and includes detailed instructions on how to implement each of the Essential 8 measures.
However, every IT environment is different, so organisations should take the guidance from the ACSC as just that - guidance. While the implementation guidelines provide a good starting point, organisations should also consider their specific needs and risk profile when implementing the Essential 8 measures.
The recommended practice for implementing the Essential 8, or any cyber security measures, is to take a risk-based approach. This means assessing the organisation's specific risks and vulnerabilities, and then implementing measures to mitigate those risks. For example, an organisation that handles sensitive personal information may prioritise implementing measures to protect that information, such as encryption and access controls, over other measures.
The Essential 8 can be self-assessed or externally assessed
While the Essential 8 cannot be certified, organisations can assess their implementation of the measures to ensure they are effectively protecting against cyber threats. The ACSC provides detailed assessment guidelines and tools to make it easier for organisations to conduct self-assessments or to engage a cyber security partner for an external assessment.
Self-assessment is the process of evaluating an organisation's cyber security measures against the Essential 8, using the guidelines and tools provided by the ACSC. This can be done by an internal team or by a third-party consultant. The self-assessment process involves identifying gaps in the organisation's current cyber security measures and developing a plan to address those gaps.
External assessment, on the other hand, is the process of engaging a cyber security partner to evaluate an organisation's cyber security measures against the Essential 8. This partner will use the guidelines and tools provided by the ACSC to assess the organisation's current cyber security measures, identify any gaps, and provide recommendations for addressing those gaps.
It's important to note that sometimes not all mitigation strategies can be met, and compensating controls must be used. However, organisations should be careful when accepting risk and transferring risk, as it should not be accepted as a substitute for implementing the Essential 8 mitigation strategies.
Constantly updated by the Australian Cyber Security Centre (ACSC)
The Essential 8 is a set of minimum baseline cyber security measures developed by the Australian Cyber Security Centre (ACSC) to protect organisations from cyber threats. It was first released in 2017 and since then, the ACSC has been constantly updating it to ensure that it remains relevant in the ever-changing cyber security landscape.
The cyber security landscape is constantly evolving, with new technology and cyber criminals becoming more sophisticated. As a result, it is important for the ACSC to constantly monitor the Australian cyber security landscape and update the Essential 8 accordingly. To do this, the ACSC conducts regular research and analysis of the cyber security environment, and reports on the findings to the public on an annual basis. This research and analysis help the ACSC to identify new threats, vulnerabilities and risks that organisations need to be aware of, which in turn helps them to update the Essential 8 accordingly.
The ACSC also update Essential 8 based on feedback and suggestions from the public and stakeholders, this feedback helps the organisation to identify gaps and areas where the Essential 8 needs to be updated to better protect organisations from cyber threats. The ACSC also publishes the change log, which provides a clear and transparent record of the changes that have been made to Essential 8, and the reasons for those changes.
Win customers
In today's business environment, organisations are increasingly seeing the importance of the supply chain. Organisations must rely on partners to succeed, and these partnerships form part of the supply chain. As a result, the supply chain must be secure, especially for partners who have access to sensitive information. Organisations are therefore reviewing their supply chain and making cyber security a key feature.
By implementing the Essential 8, organisations can demonstrate their commitment to cyber security, which can help to build confidence in their customers. This is especially important for organisations that work with sensitive information, such as personal data or financial information. By showing that they have taken the necessary steps to protect this information, organisations can win more projects and contracts.
Resources
"ACSC Annual Cyber Threat Report, July 2021 to June 2022", by the Australian Cyber Security Centre.
"Parliament approves Government’s privacy penalty bill", by the Hon Mark Dreyfus KC MP, Australian Government.
"Essential Eight to IMS Mapping", by the Australian Cyber Security Centre.
"Essential Eight", by the Australian Cyber Security Centre.
"Inside the Optus hack that woke up Australia", by Paul Smith, The Australian Financial Review.

